A new “comprehensive toolset” called AlienFox is being distributed on Telegram as a way for threat actors to harvest credentials from API keys and secrets from popular cloud service providers.
The cybersecurity company characterized the malware as highly modular and constantly evolving to accommodate new features and performance improvements.
The primary use of AlienFox is to enumerate misconfigured hosts via scanning platforms like LeakIX and SecurityTrails, and subsequently leverage various scripts in the toolkit to extract credentials from configuration files exposed on the servers.
Recent versions of the tool incorporate the ability to establish persistence on an Amazon Web Services (AWS) account and escalate privileges as well as automate spam campaigns through the compromised accounts.

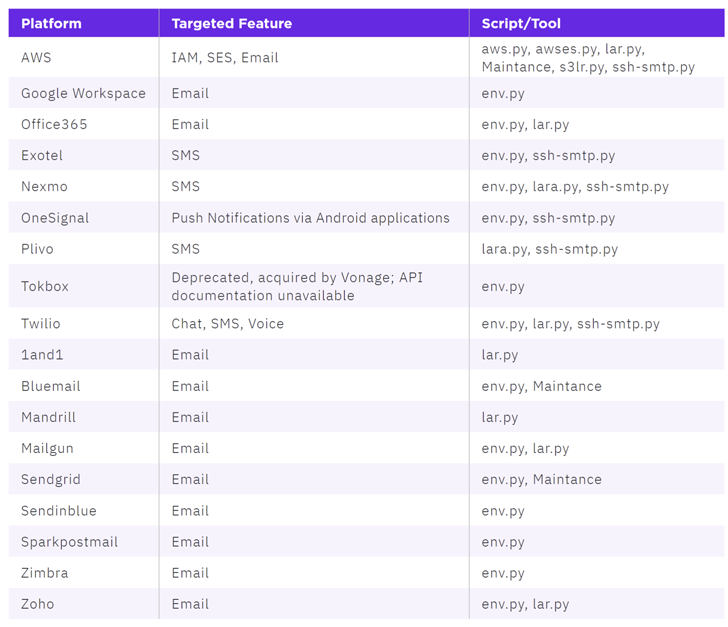
Attacks involving AlienFox are said to be opportunistic, with the scripts capable of gathering sensitive data pertaining to AWS, Bluemail, Exotel, Google Workspace, Mailgun, Mandrill, Microsoft 365, Sendgrid, Twilio, Zimbra, and Zoho.
Two such scripts are AndroxGh0st and GreenBot, which were previously documented by Lacework and Permiso p0 Labs.
To mitigate threats posed by AlienFox, organizations are recommended to adhere to configuration management best practices and follow the principle of least privilege (PoLP).
“The AlienFox toolset demonstrates another stage in the evolution of cybercrime in the cloud,” Delamotte said. “For victims, compromise can lead to additional service costs, loss in customer trust, and remediation costs.”
Source: https://thehackernews.com/