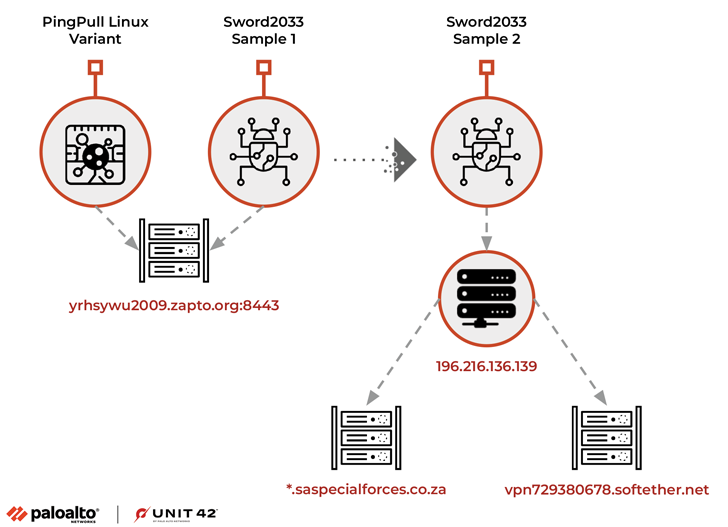
The Chinese nation-state group dubbed Alloy Taurus is using a Linux variant of a backdoor called PingPull as well as a new undocumented tool codenamed Sword2033.
Alloy Taurus is the constellation-themed moniker assigned to a threat actor that’s known for its attacks targeting telecom companies since at least 2012. It’s also tracked by Microsoft as Granite Typhoon (previously Gallium).
PingPull, first documented by Unit 42 in June 2022, is a remote access trojan that employs the Internet Control Message Protocol (ICMP) for command-and-control (C2) communications.
The Linux flavor of the malware, which was uploaded to VirusTotal on March 7, 2023, boasts of similar functionalities as its Windows counterpart, allowing it to carry out file operations and run arbitrary commands by transmitting from the C2 server a single upper case character between A and K, and M.

The malware’s links to Alloy Taurus stems from the fact that the domain resolved to an IP address that was previously identified as an active indicator of compromise (IoC) associated with a 2021 campaign targeting companies operating in Southeast Asia, Europe, and Africa.
The targeting of South Africa, per the cybersecurity company, comes against the backdrop of the country holding a joint 10-day naval drill with Russia and China earlier this year.
“Alloy Taurus remains an active threat to telecommunications, finance, and government organizations across Southeast Asia, Europe, and Africa,” Unit 42 said.
“The identification of a Linux variant of PingPull malware, as well as recent use of the Sword2033 backdoor, suggests that the group continues to evolve their operations in support of their espionage activities.”
Source: https://thehackernews.com/