In yet another sign of a lucrative crimeware-as-a-service (CaaS) ecosystem, cybersecurity researchers have discovered a new Windows-based information stealer called Meduza Stealer that’s actively being developed by its author to evade detection by software solutions.
“The Meduza Stealer has a singular objective: comprehensive data theft,” Uptycs said in a new report. “It pilfers users’ browsing activities, extracting a wide array of browser-related data.”
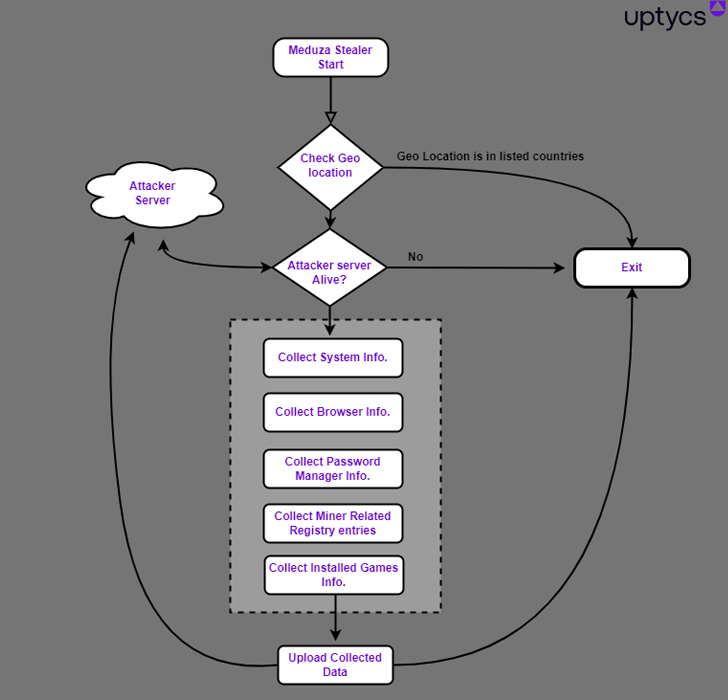
Despite the similarity in features, Meduza boasts of a “crafty” operational design that eschews the use of obfuscation techniques and promptly terminates its execution on compromised hosts should a connection to the attacker’s server fail.
It’s also designed to abort if a victim’s location is in the stealer’s predefined list of excluded countries, which consists of the Commonwealth of Independent States (CIS) and Turkmenistan.
Meduza Stealer, besides gathering data from 19 password manager apps, 76 crypto wallets, 95 web browsers, Discord, Steam, and system metadata, harvests miner-related Windows Registry entries as well as a list of installed games, indicating a broader financial motive.

It’s currently being offered for sale on underground forums such as XSS and Exploit.in and a dedicated Telegram channel as a recurring subscription that costs $199 per month, $399 for three months, or $1,199 for a lifetime license. The information pilfered by the malware is made available through a user-friendly web panel.
“This in-depth feature set showcases the sophisticated nature of the Meduza Stealer and the lengths its creators are willing to go to ensure its success.”
Source: https://thehackernews.com/