Government entities and large organizations have been targeted by an unknown threat actor by exploiting a security flaw in Fortinet FortiOS software to result in data loss and OS and file corruption.
“The complexity of the exploit suggests an advanced actor and that it is highly targeted at governmental or government-related targets,” Fortinet researchers Guillaume Lovet and Alex Kong said in an advisory last week.
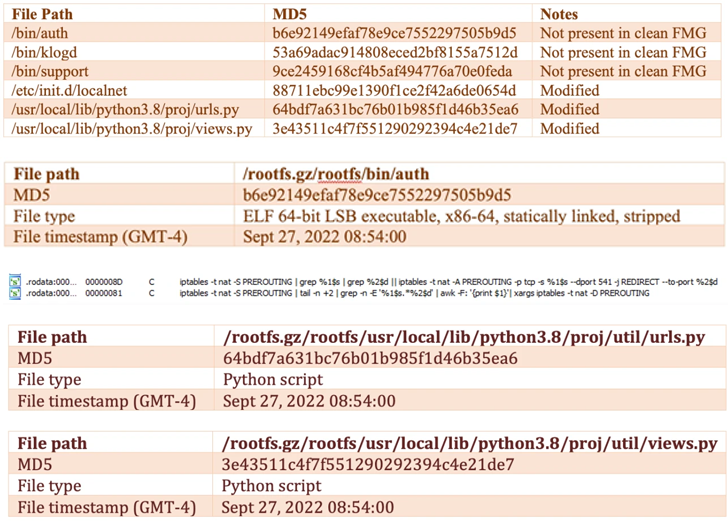
“An improper limitation of a pathname to a restricted directory vulnerability (‘path traversal’) [CWE-22] in FortiOS may allow a privileged attacker to read and write arbitrary files via crafted CLI commands,” the company noted.

The /bin/fgfm malware is designed to establish contact with a remote server to download files, exfiltrate data from the compromised host, and grant remote shell access.
Additional changes introduced to the firmware are said to have provided the attacker with persistent access and control, not to mention even disable firmware verification at startup.
Source: https://thehackernews.com/