Cybersecurity researchers have discovered previously undocumented payloads associated with a Romanian threat actor named Diicot, revealing its potential for launching distributed denial-of-service (DDoS) attacks.
“The Diicot name is significant, as it’s also the name of the Romanian organized crime and anti-terrorism policing unit,” Cado Security said in a technical report.
“In addition, artifacts from the group’s campaigns contain messaging and imagery related to this organization.”
Diicot (née Mexals) was first documented by Bitdefender in July 2021, uncovering the actor’s use of a Go-based SSH brute-forcer tool called Diicot Brute to breach Linux hosts as part of a cryptojacking campaign.
“The attackers use a long chain of payloads before eventually dropping a Monero cryptominer,” Akamai researcher Stiv Kupchik said at the time.
“New capabilities include usage of a Secure Shell Protocol (SSH) worm module, increased reporting, better payload obfuscation, and a new LAN spreader module.”
The latest analysis from Cado Security shows that the group is also deploying an off-the-shelf botnet referred to as Cayosin, a malware family that shares characteristics with Qbot and Mirai.

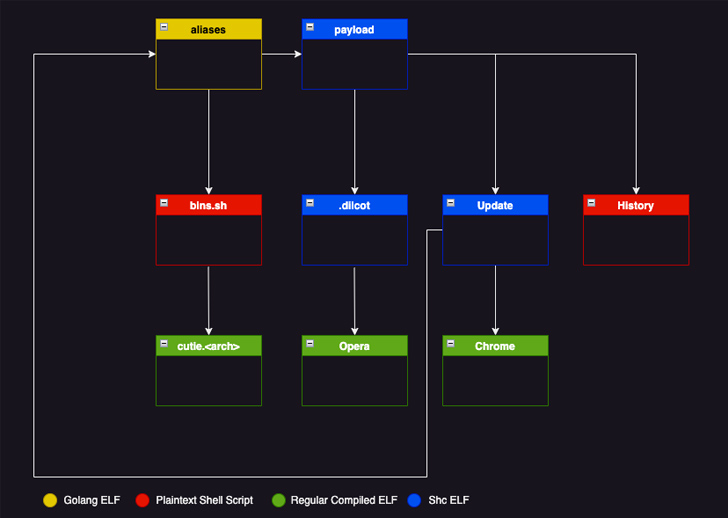
Diicot’s compromise chains have remained largely consistent, leveraging the custom SSH brute-forcing utility to gain a foothold and drop additional malware such as the Mirai variant and the crypto miner.
Some of the other tools used by the actor are as follows –
- Chrome – An internet scanner based on Zmap that can write the results of the operation to a text file (“bios.txt”).
- Update – An executable that fetches and executes the SSH brute-forcer and Chrome if they don’t exist in the system.
- History – A shell script that’s designed to run Update
This is then followed by running a series of commands to profile the infected host and using it to either deploy a cryptominer or make it act as a spreader if the machine’s CPU has less than four cores.
To mitigate such attacks, organizations are recommended to implement SSH hardening and firewall rules to limit SSH access to specific IP addresses.
Source: https://thehackernews.com/