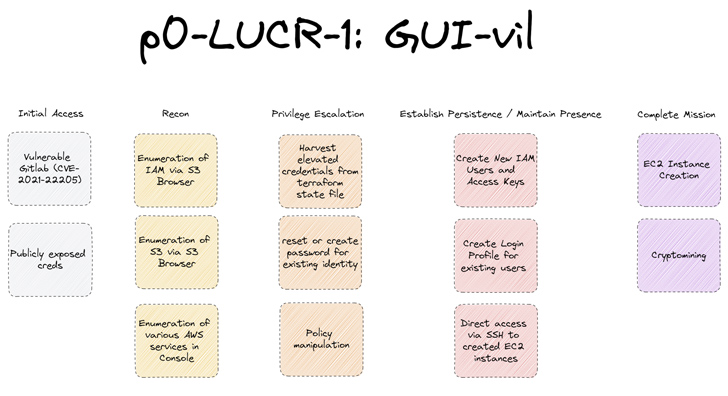
A financially motivated threat actor of Indonesian origin has been observed leveraging Amazon Web Services (AWS) Elastic Compute Cloud (EC2) instances to carry out illicit crypto mining operations.
Cloud security company’s Permiso P0 Labs, which first detected the group in November 2021, has assigned it the moniker GUI-vil (pronounced Goo-ee-vil).
“The group displays a preference for Graphical User Interface (GUI) tools, specifically S3 Browser (version 9.5.5) for their initial operations,” the company said in a report shared with The Hacker News. “Upon gaining AWS Console access, they conduct their operations directly through the web browser.”
Attack chains mounted by GUI-vil entail obtaining initial access by weaponizing AWS keys in publicly exposed source code repositories on GitHub or scanning for GitLab instances that are vulnerable to remote code execution flaws (e.g., CVE-2021-22205).

“GUI-vil will also create access keys for the new identities they are creating so they can continue usage of S3 Browser with these new users,” P0 Labs researchers Ian Ahl and Daniel Bohannon explained.
Alternatively, the group has also been spotted creating login profiles for existing users that do not have them so as to enable access to the AWS console without raising red flags.
GUI-vil’s links to Indonesia stem from the fact that the source IP addresses associated with the activities are linked to two Autonomous System Numbers (ASNs) located in the Southeast Asian country.
Source: https://thehackernews.com/