Threat actors using hacking tools from an Israeli surveillanceware vendor named QuaDream targeted at least five members of civil society in North America, Central Asia, Southeast Asia, Europe, and the Middle East.
According to findings from a group of researchers from the Citizen Lab, the spyware campaign was directed against journalists, political opposition figures, and an NGO worker in 2021. The names of the victims were not disclosed.
It’s also suspected that the company abused a zero-click exploit dubbed ENDOFDAYS in iOS 14 to deploy spyware as a zero-day in version 14.4 and 14.4.2. There is no evidence that the exploit has been used after November 2021.
The malware, named KingsPawn, contains a monitor agent and the primary malware agent, both of which are Mach-O files written in Objective-C and Go, respectively.
While the monitor agent is responsible for reducing the forensic footprint of the malware to evade detection, the main agent comes with capabilities to gather device information, cellular and Wi-Fi data, harvest files, access camera in the background, access location, call logs, and iOS Keychain, and even generate an iCloud time-based one-time password (TOTP).

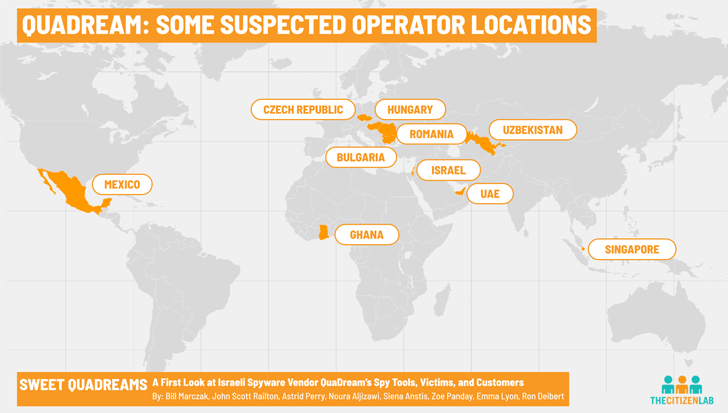
Internet scans carried out by the Citizen Lab reveal that QuaDream’s customers operated 600 servers from several countries around the world between late 2021 and early 2023, including Bulgaria, Czech Republic, Hungary, Romania, Ghana, Israel, Mexico, Singapore, the U.A.E., and Uzbekistan.
Despite attempts made by the spyware to cover its tracks, the interdisciplinary laboratory said it was able to uncover unspecified traces of what it calls the “Ectoplasm Factor” that could be used to track QuaDream’s toolset in the future.
Calling the growth of mercenary spyware companies as a threat to democracy and human rights, Microsoft said combating such offensive actors requires a “collective effort” and a “multistakeholder collaboration.”
“This poses real risk to human rights online, but also to the security and stability of the broader online environment. The services they offer require cyber mercenaries to stockpile vulnerabilities and search for new ways to access networks without authorization.”
Source: https://thehackernews.com/