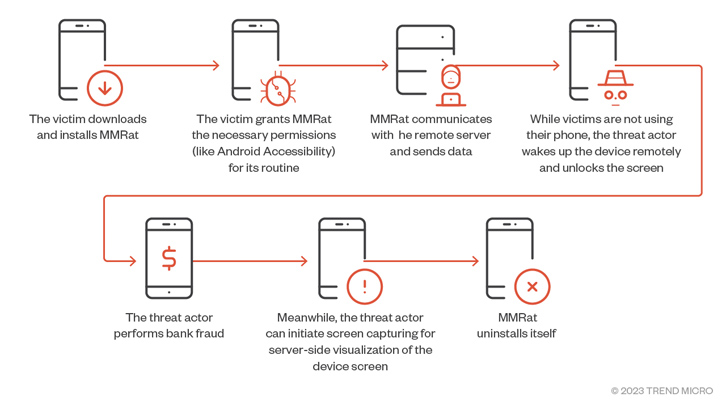
A previously undocumented Android banking trojan dubbed MMRat has been observed targeting mobile users in Southeast Asia since late June 2023 to remotely commandeer the devices and perform financial fraud.
What makes MMRat stand apart from others of its kind is the use of a customized command-and-control (C2) protocol based on protocol buffers (aka protobuf) to efficiently transfer large volumes of data from compromised handsets, demonstrating the growing sophistication of Android malware.
The entry point of the attacks is a network of phishing sites that mimic official app stores, although how victims are directed to these links is presently unknown. MMRat typically masquerades as an official government or a dating app.
Once installed, the app leans heavily on Android accessibility service and MediaProjection API, both of which have been leveraged by another Android financial trojan called SpyNote, to carry out its activities. The malware is also capable of abusing its accessibility permissions to grant itself other permissions and modify settings.

It further sets up persistence to survive between reboots and initiates communications with a remote server to await instructions and exfiltrate the results of the execution of those commands back to it. The trojan employs different combinations of ports and protocols for functions such as data exfiltration, video streaming, and C2 control.
The attacks end with MMRat deleting itself upon receiving the C2 command UNINSTALL_APP, which typically takes place after a successful fraudulent transaction, effectively removing all traces of infection from the device.
To mitigate threats posed by such potent malware, it’s recommended that users only download apps from official sources, scrutinize app reviews, and check the permissions an app requests for access to before usage.
Source: https://thehackernews.com/