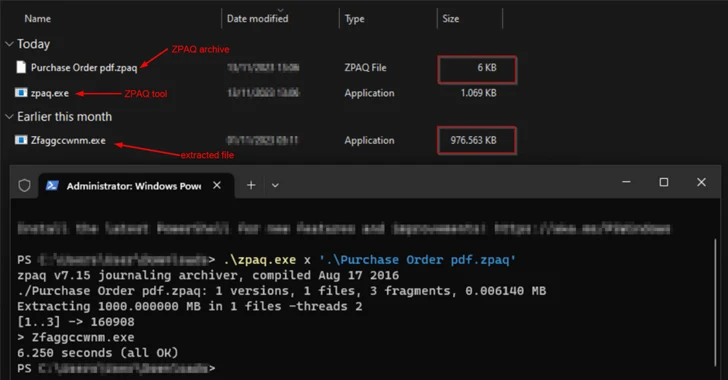
A new variant of the Agent Tesla malware has been observed delivered via a lure file with the ZPAQ compression format to harvest data from several email clients and nearly 40 web browsers.
First appearing in 2014, Agent Tesla is a keylogger and remote access trojan (RAT) written in .NET that’s offered to other threat actors as part of a malware-as-a-service (MaaS) model.
Agent Tesla is typically delivered via phishing emails, with recent campaigns leveraging a six-year-old memory corruption vulnerability in Microsoft Office’s Equation Editor (CVE-2017-11882).

The latest attack chain begins with an email containing a ZPAQ file attachment that purports to be a PDF document, opening which extracts a bloated .NET executable that’s mostly padded with zero bytes to artificially inflate the sample size to 1 GB in an effort to bypass traditional security measures.
The end goal of the attack is to infect the endpoint with Agent Teslathat’s obfuscated with .NET Reactor, a legitimate code protection software. Command-and-control (C2) communications is accomplished via Telegram.
The development is a sign that threat actors are experimenting with uncommon file formats for malware delivery, necessitating that users be on the lookout for suspicious emails and keep their systems up-to-date.
Source: https://thehackernews.com/