Ransomware groups are increasingly switching to remote encryption in their attacks, marking a new escalation in tactics adopted by financially motivated actors to ensure the success of their campaigns.
“Companies can have thousands of computers connected to their network, and with remote ransomware, all it takes is one underprotected device to compromise the entire network,” Mark Loman, vice president of threat research at Sophos, said.
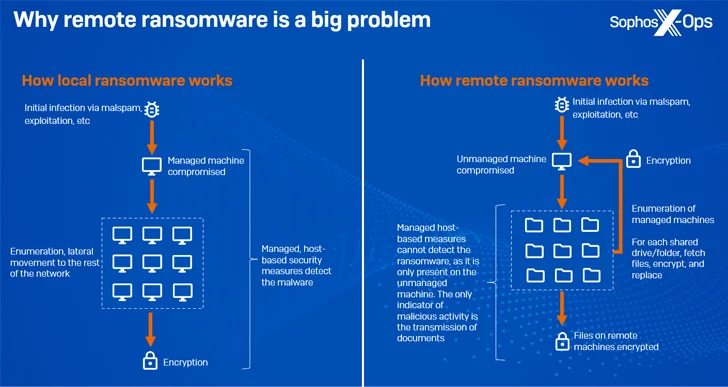
Remote encryption (aka remote ransomware), as the name implies, occurs when a compromised endpoint is used to encrypt data on other devices on the same network.
A significant advantage to this approach is that it renders process-based remediation measures ineffective and the managed machines cannot detect the malicious activity since it is only present in an unmanaged device.

This also extends to publishing FAQs and press releases on their data leak sites, even including direct quotes from the operators, and correcting mistakes made by journalists. Another tactic is the use of catchy names and slick graphics, indicating an evolution of the professionalization of cyber crime.
“The RansomHouse group, for example, has a message on its leak site specifically aimed at journalists, in which it offers to share information on a ‘PR Telegram channel’ before it is officially published,” Sophos noted.
While ransomware groups like Conti and Pysa are known for adopting an organizational hierarchy comprising senior executives, system admins, developers, recruiters, HR, and legal teams, there is evidence to suggest that some have advertised opportunities for English writers and speakers on criminal forums.
Source: https://thehackernews.com/