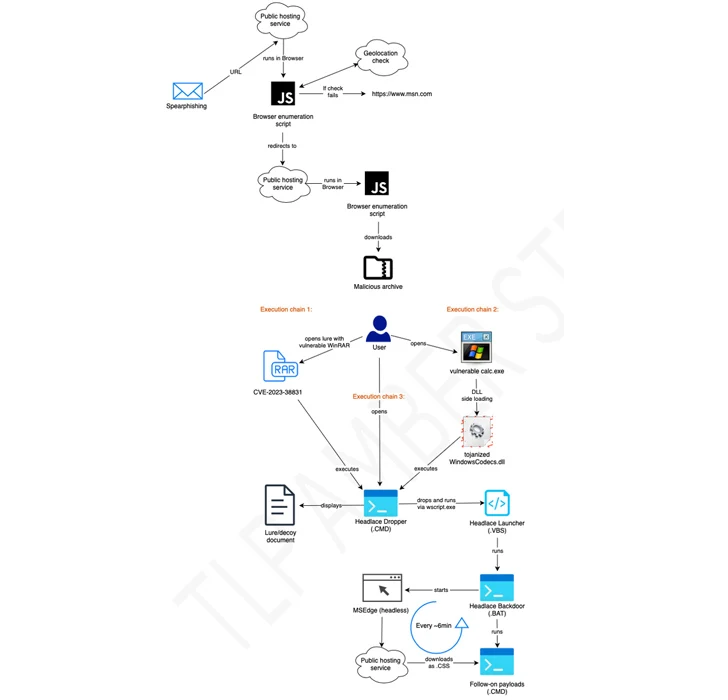
The Russian nation-state threat actor known as APT28 has been observed making use of lures related to the ongoing Israel-Hamas war to facilitate the delivery of a custom backdoor called HeadLace.
IBM X-Force is tracking the adversary under the name ITG05, which is also known as BlueDelta, Fancy Bear, Forest Blizzard (formerly Strontium), FROZENLAKE, Iron Twilight, Sednit, Sofacy, and TA422.
“The newly discovered campaign is directed against targets based in at least 13 nations worldwide and leverages authentic documents created by academic, finance and diplomatic centers,” security researchers Golo Mühr, Claire Zaboeva, and Joe Fasulo said.
Some of the attacks have been found to employ RAR archives exploiting the WinRAR flaw called CVE-2023-38831 to propagate HeadLace, a backdoor that was first disclosed by the computer Emergency Response Team of Ukraine (CERT-UA) in attacks aimed at critical infrastructure in the country.

The disclosure comes a week after Microsoft, Palo Alto Networks Unit 42, and Proofpoint detailed the threat actor’s exploitation of a critical security flaw of Microsoft Outlook (CVE-2023-23397, CVSS score: 9.8) to gain unauthorized access to victims’ accounts within Exchange servers.
The development also follows a new advisory in which CERT-UA linked the threat actor known as UAC-0050 to a massive email-based phishing attack against Ukraine and Poland using Remcos RAT and Meduza Stealer.
Source: https://thehackernews.com/