A new open source remote access trojan (RAT) called DogeRAT targets Android users primarily located in India as part of a sophisticated malware campaign.
The malware is distributed via social media and messaging platforms under the guise of legitimate applications like Opera Mini, OpenAI ChatGOT, and Premium versions of YouTube, Netflix, and Instagram.
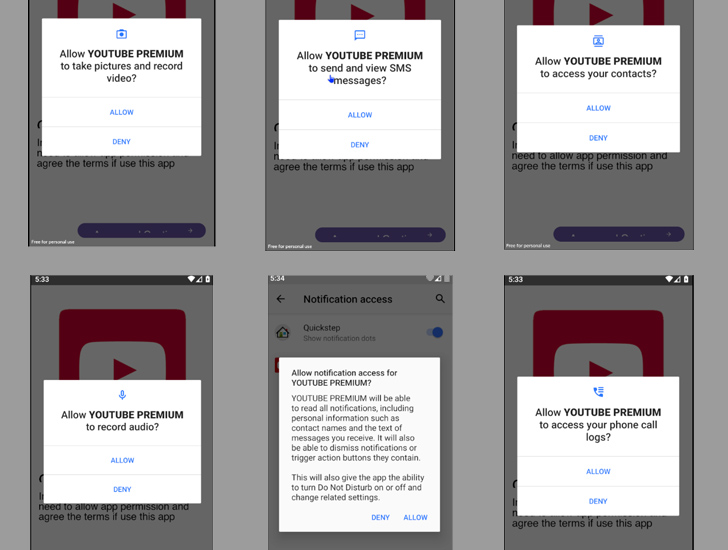
“Once installed on a victim’s device, the malware gains unauthorized access to sensitive data, including contacts, messages, and banking credentials,” cybersecurity firm CloudSEK said in a Monday report.
DogeRAT, like many other malware-as-a-service (MaaS) offerings, is promoted by its India-based developer through a Telegram channel that has more than 2,100 subscribers since it was created on June 9, 2022.
This also includes a premium subscription that’s sold for dirt-cheap prices ($30) with additional capabilities such as taking screenshots, stealing images, capturing clipboard content, and logging keystrokes.

In a further attempt to make it more accessible to other criminal actors, the free version of DogeRAT has been made available on GitHub, alongside screenshots and video tutorials showcasing its functions.
The findings come as Google-owned Mandiant detailed a new Android backdoor called LEMONJUICE that’s designed to enable remote control of and access to a compromised device.
“The malware is capable of tracking device location, recording the microphone, retrieving contact lists, accessing call, SMS, clipboard, and notification logs, viewing installed applications, downloading and uploading files, viewing connectivity status, and executing additional commands from the C2 server,” researcher Jared Wilson said.
Source: https://thehackernews.com/