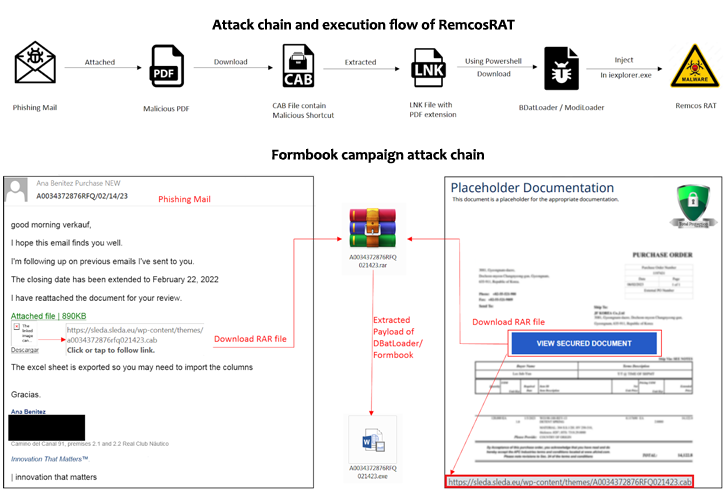
A new phishing campaign has set its sights on European entities to distribute Remcos RAT and Formbook via a malware loader dubbed DBatLoader.
“The malware payload is distributed through WordPress websites that have authorized SSL certificates, which is a common tactic used by threat actors to evade detection engines,” Zscaler researchers Meghraj Nandanwar and Satyam Singh said in a report published Monday.
The findings build upon a previous report from SentinelOne last month that detailed phishing emails containing malicious attachments that masquerade as financial documents to activate the infection chain.
DBatLoader, also called ModiLoader and NatsoLoader, is a Delphi-based malware that’s capable of delivering follow-on payloads from cloud services like Google Drive and Microsoft OneDrive, while also adopting image steganography techniques to evade detection engines.

This enables the attackers to conduct elevated activities without alerting users, including establishing persistence and adding the “C:\Users” directory to the Microsoft Defender exclusion list to avoid getting scanned.
To mitigate risks posed by DBatLoader, it’s advised to monitor process executions that involve filesystem paths with trailing spaces and consider configuring Windows UAC to Always notify.
Source: https://thehackernews.com/