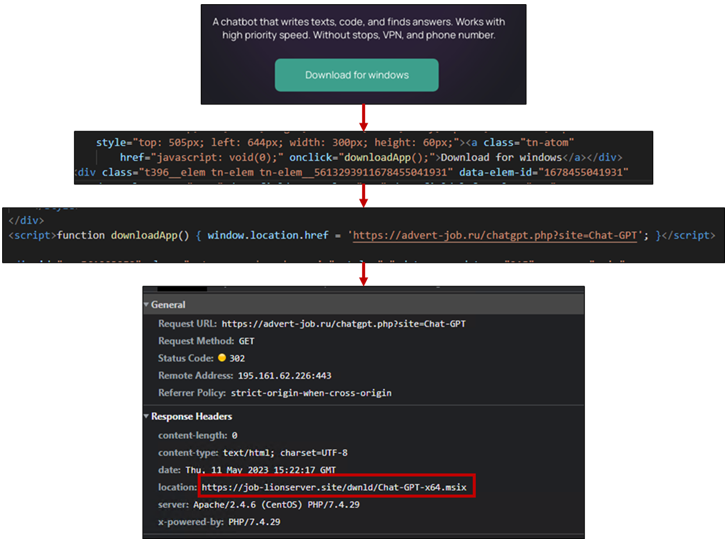
Malicious Google Search ads for generative AI services like OpenAI ChatGPT and Midjourney are being used to direct users to sketchy websites as part of a BATLOADER campaign designed to deliver RedLine Stealer malware.
“Both AI services are extremely popular but lack first-party standalone apps (i.e., users interface with ChatGPT via their web interface while Midjourney uses Discord),” eSentire said in an analysis.
The installer file, per eSentire, is rigged with an executable file (ChatGPT.exe or midjourney.exe) and a PowerShell script (Chat.ps1 or Chat-Ready.ps1) that downloads and loads RedLine Stealer from a remote server.
Once the installation is complete, the binary makes use of Microsoft Edge WebView2 to load chat.openai[.]com or www.midjourney[.]com – the legitimate ChatGPT and Midjourney URLs – in a pop-up window so as to not raise any red flags.

The adversary’s use of ChatGPT and Midjourney-themed lures to serve malicious ads and ultimately drop the RedLine Stealer malware was also highlighted last week by Trend Micro.
This is not the first time the operators behind BATLOADER have capitalized on the AI craze to distribute malware. In March 2023, eSentire detailed a similar set of attacks that leveraged ChatGPT lures to deploy Vidar Stealer and Ursnif.
The findings come weeks after Securonix uncovered a phishing campaign dubbed OCX#HARVESTER that targeted the cryptocurrency sector between December 2022 and March 2023 with More_eggs (aka Golden Chickens), a JavaScript downloader that’s used to serve additional payloads.
eSentire, in January, traced the identity of one of the key operators of the malware-as-a-service (MaaS) to an individual located in Montreal, Canada. The second threat actor associated with the group has since been identified as a Romanian national who goes by the alias Jack.
Source: https://thehackernews.com/