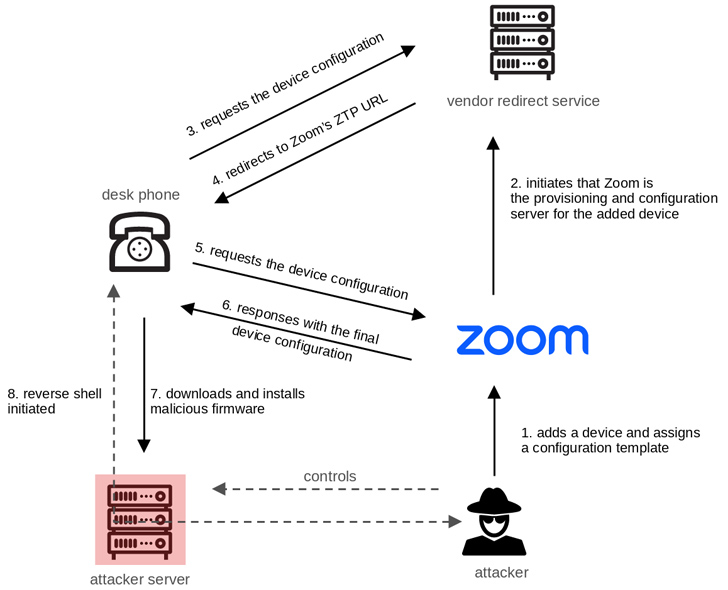
Multiple security vulnerabilities have been disclosed in AudioCodes desk phones and Zoom’s Zero Touch Provisioning (ZTP) that could be potentially exploited by a malicious attacker to conduct remote attacks.
“An external attacker who leverages the vulnerabilities discovered in AudioCodes Ltd.’s desk phones and Zoom’s Zero Touch Provisioning feature can gain full remote control of the devices,” SySS security researcher Moritz Abrell said in an analysis published Friday.
The unfettered access could then be weaponized to eavesdrop on rooms or phone calls, pivot through the devices and attack corporate networks, and even build a botnet of infected devices. The research was presented at the Black Hat USA security conference earlier this week.
Specifically, the provisioning process was found to lack client-side authentication mechanisms during the retrieval of configuration files from the ZTP service, thereby leading to a scenario where an attacker could potentially trigger the download of malicious firmware from a rogue server.

The study further uncovered improper authentication issues in the cryptographic routines of AudioCodes VoIP desk phones (which support Zoom ZTP) that allow for the decryption of sensitive information, such as passwords and configuration files transmitted via a redirection server used by the phone to fetch the configuration.
The disclosure arrives nearly a year after the German cybersecurity company identified a security issue in Microsoft Teams Direct Routing functionality that could render installations susceptible to toll fraud attacks.
“An external, unauthenticated attacker is able to send specially crafted SIP messages that pretend to originate from Microsoft and are therefore correctly classified by the victim’s Session Border Controller,” Abrell noted at the time. “As a result, unauthorized external calls are made through the victim’s phone line.”
Source: https://thehackernews.com/