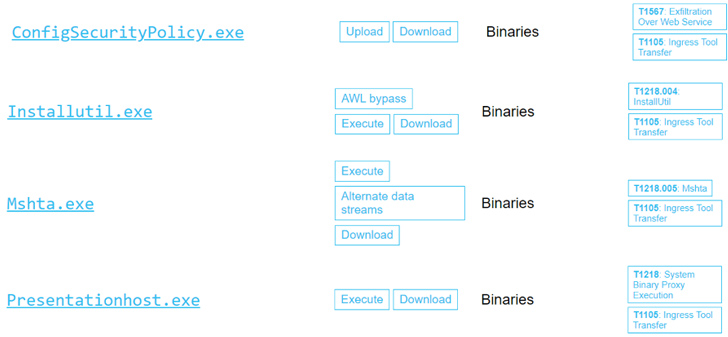
Cybersecurity researchers have discovered a set of 11 living-off-the-land binaries-and-scripts (LOLBAS) that could be maliciously abused by threat actors to conduct post-exploitation activities.
To that end, the Israeli cybersecurity company said it uncovered nine LOLBAS downloaders and three executors that could enable adversaries to download and execute “more robust malware” on infected hosts.
This includes: MsoHtmEd.exe, Mspub.exe, ProtocolHandler.exe, ConfigSecurityPolicy.exe, InstallUtil.exe, Mshta.exe, Presentationhost.exe, Outlook.exe, MSAccess.exe, scp.exe, and sftp.exe.

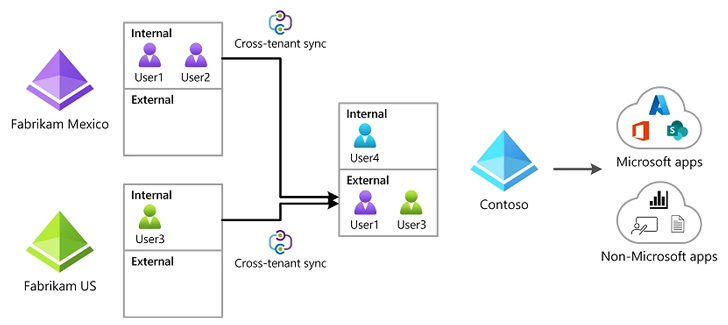
The findings come as Vectra disclosed a potential new attack vector that leverages Microsoft Entra ID (previously Azure Active Directory) cross-tenant synchronization (CTS) feature to facilitate lateral movement to other tenants assuming a privileged identity has already been compromised in the cloud environment.

“An attacker operating in a compromised environment can exploit an existing CTS configuration tenant to move laterally from one tenant to another connected tenant,” the company said. Alternatively, “an attacker operating in a compromised tenant can deploy a rogue Cross Tenant Access configuration to maintain persistent access.”
Source: https://thehackernews.com/