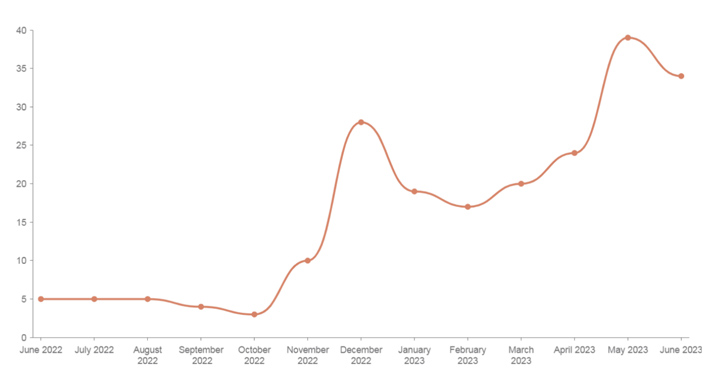
Mallox ransomware activities in 2023 have witnessed a 174% increase when compared to the previous year, new findings from Palo Alto Networks Unit 42 reveal.
“Mallox ransomware, like many other ransomware threat actors, follows the double extortion trend: stealing data before encrypting an organization’s files, and then threatening to publish the stolen data on a leak site as leverage to convince victims to pay the ransom fee,” security researchers Lior Rochberger and Shimi Cohen said in a new report shared with The Hacker News.
A notable aspect of the group is its pattern of exploiting poorly secured MS-SQL servers via dictionary attacks as a penetration vector to compromise victims’ networks. Xollam is a deviation from the norm in that it has been observed using malicious OneNote file attachments for initial access, as detailed by Trend Micro last month.
 ‘
‘
The binary, for its part, attempts to stop and remove SQL-related services, delete volume shadow copies, clear system event logs, terminate security-related processes, and bypass Raccine, an open-source tool designed to counter ransomware attacks, prior to commencing its encryption process, after which a ransom note is dropped in every directory.
TargetCompany remains a small, closed group, but it has also been observed recruiting affiliates for the Mallox ransomware-as-a-service (RaaS) affiliate program on the RAMP cybercrime forum.
The development comes as ransomware continues to be a lucrative financial scheme, netting cybercriminals no less than $449.1 million in the first half of 2023 alone, per Chainalysis.
The sudden surge in Mallox infections is also symptomatic of a broader trend where ransomware attacks have witnessed a 221% jump year-over-year as of June 2023, with 434 attacks reported in June 2023 alone, largely driven by Cl0p’s exploitation of the MOVEit file transfer software vulnerability.
Source: https://thehackernews.com/

 ‘
‘







