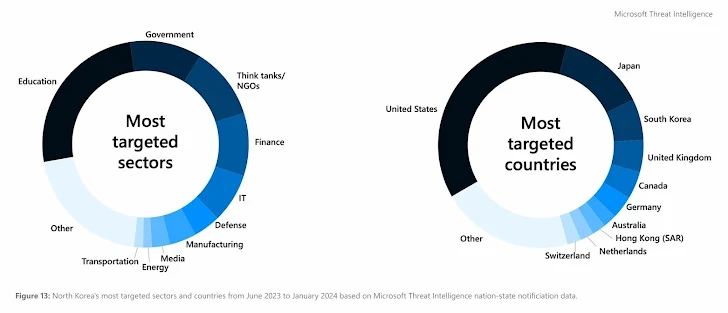
Microsoft has revealed that North Korea-linked state-sponsored cyber actors have begun to use artificial intelligence (AI) to make its operations more effective and efficient.
“They are learning to use tools powered by AI large language models (LLM) to make their operations more efficient and effective,” the tech giant said in its latest report on East Asia hacking groups.
The company specifically highlighted a group named Emerald Sleet (aka Kimusky or TA427), which has been observed using LLMs to bolster spear-phishing efforts aimed at Korean Peninsula experts.
It further employed LLMs to troubleshoot technical issues, conduct basic scripting tasks, and draft content for spear-phishing messages, Redmond said, adding it worked with OpenAI to disable accounts and assets associated with the threat actor.
According to a report published by enterprise security firm Proofpoint last week, the group “engages in benign conversation starter campaigns to establish contact with targets for long-term exchanges of information on topics of strategic importance to the North Korean regime.”
Kimsuky’s modus operandi involves leveraging think tank and non-governmental organization-related personas to legitimize its emails and increase the likelihood of success of the attack.

In another instance, a Germany-based IT company was compromised by Diamond Sleet (aka Lazarus Group) in August 2023 and weaponized an application from a Taiwan-based IT firm to conduct a supply chain attack in November 2023.
The Lazarus Group is also notable for employing intricate methods like Windows Phantom DLL Hijacking and Transparency, Consent, and Control (TCC) database manipulation in Windows and macOS, respectively, to undermine security protections and deploy malware, contributing to its sophistication and elusive nature, per Interpres Security.
The findings come against the backdrop of a new campaign orchestrated by the Konni (aka Vedalia) group that uses Windows shortcut (LNK) files to deliver malicious payloads.
Source: https://thehackernews.com/