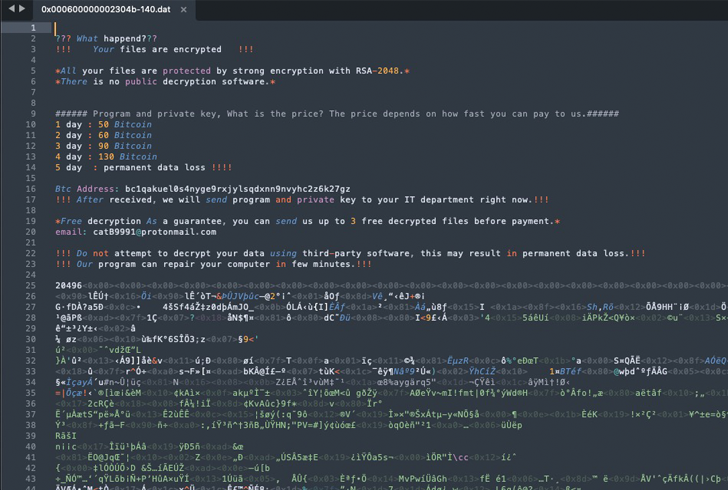
The threat actors behind the CatB ransomware operation have been observed using a technique called DLL search order hijacking to evade detection and launch the payload.
CatB, also referred to as CatB99 and Baxtoy, emerged late last year and is said to be an “evolution or direct rebrand” of another ransomware strain known as Pandora based on code-level similarities.
One of the key defining characteristics of CatB is its reliance on DLL hijacking via a legitimate service called Microsoft Distributed Transaction Coordinator (MSDTC) to extract and launch the ransomware payload.

“The [MSDTC] configurations changed are the name of the account under which the service should run, which is changed from Network Service to Local System, and the service start option, which is changed from Demand start to Auto start for persistency if a restart occurs,” Minerva Labs researcher Natalie Zargarov explained in a previous analysis.

This is not the first time the MSDTC service has been weaponized for malicious purposes. In May 2021, Trustwave disclosed a novel malware dubbed Pingback that leveraged the same technique to achieve persistence and bypass security solutions.
Source: https://thehackernews.com/